There are always people who want to piggy-back on the achievements of others. After ESET warned the public against ACAD/Medre.A in two blogs here and here and issued a free standalone cleaner for remediation, there was always the possibility that drawing attention to the issue would result in the topic being misused for other purposes. While ACAD/Medre.A had impact on one industry in one geographical location, and the threat has already effectively been neutralized, ESET researchers found a puzzling website that claims to help in removing this threat.
If we review the claims made on the website about ACAD/Medre.A, we read first that:
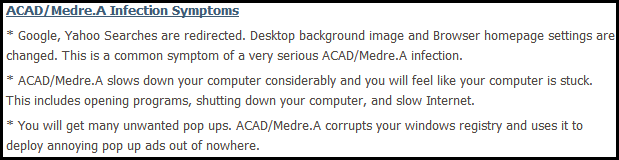
While these are common symptoms of malicious software that hijacks a computer and misuses it for nefarious purposes, ACAD/Medre.A causes none of these symptoms!
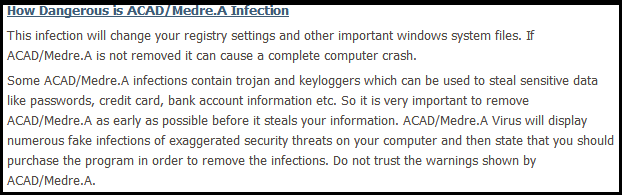
Again, while this is a description of many forms of malware, ACAD/Medre.A does not perform any of the actions described above.
Are we getting down to the bottom line here?
Ah yes… Download… We will get back to this later.
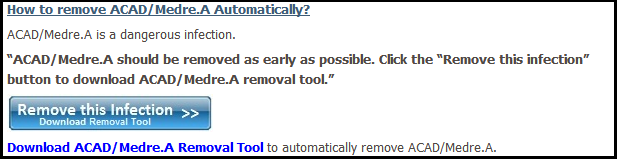
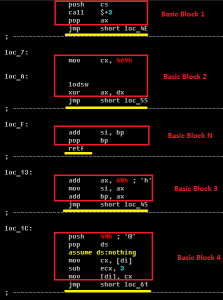
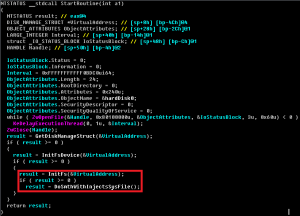
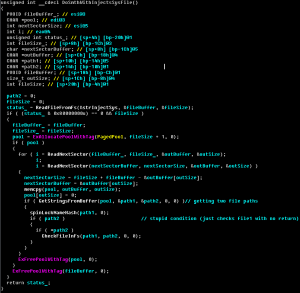
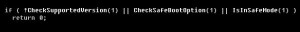
First, what should we do to manually remove ACAD/Medre.A? In fact, apart from removing some registry keys (although even those will not hurt the system if they are left behind), removing the “acad.fas” files is enough. They are fastload AutoLISP compiled files, not locked by the system, not loaded as a process, and not installed as software on the system.
The advice from the website:
Needless to say there is no ACAD/Medre.A process to stop, there is no ACAD/Medre.A program to uninstall, and there are no real ACAD/Medre.A registry files, so the only “sensible” advice is to search for the ACAD/Medre.A files on your system and delete these.
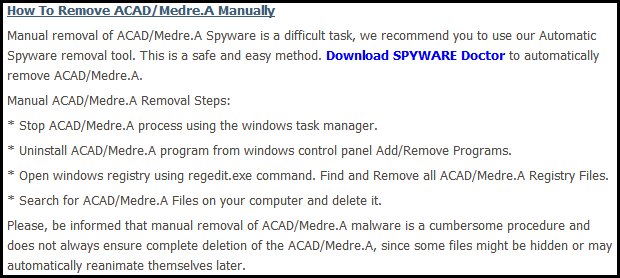
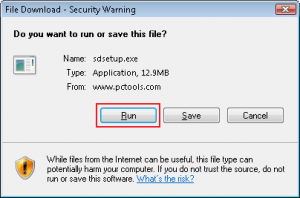
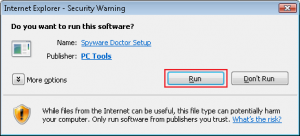
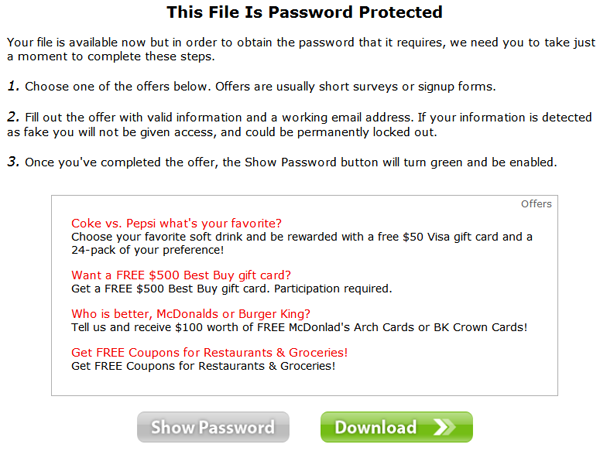
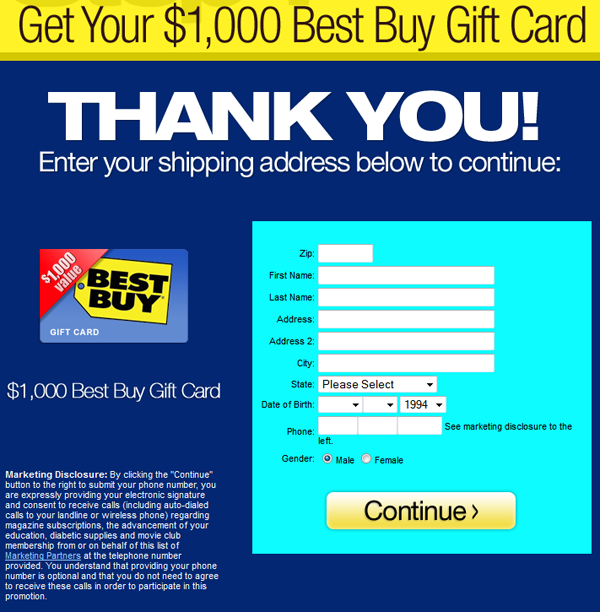
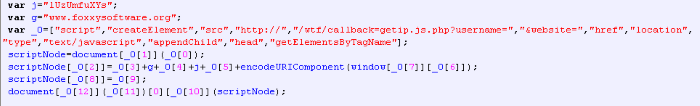
So far for the advice, oh no… wait, there is more…. There is the advice to download “SPYWARE Doctor” to do all this automatically. You are given comprehensive information on the actions necessary to install “SPYWARE Doctor”, complete with accompanying screenshots:
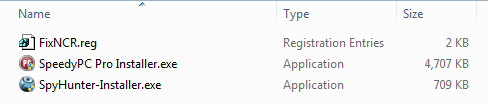
A small detail here is that Spyware Doctor, a genuine utility published by PC Tools, a Symantec company, is not what gets downloaded or installed at all. What actually gets downloaded (and installed if you choose) are three different “tools”.
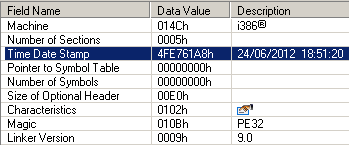
The “FixNCR.reg” file is a registry editing file that clears a large set of registry entries commonly used by malicious code, but none of them is used by ACAD/Medre.A. Medre. A only uses the following Registry entries to store its internal data, such as timestamps:
[HKCU\Software\Microsoft\Windows\Windows Error Reporting]
“FILE”
“FILE-G”
“FILE-H”
“Time”
Note that as mentioned in Robert Liposvsky’s Technical Analysis blog, the [HKCU\Software\Microsoft\Windows\Windows Error Reporting] Registry key is a legitimate one, only the four above-mentioned entries are used by the malware. None of these four entries are cleaned by this registry fix. As they are just used as storage for internal data by the malware, there is no harm in not removing them, but of course, given the way in which the cleaner is advertised , as mentioned above, any user would expect these entries to be fixed, too!
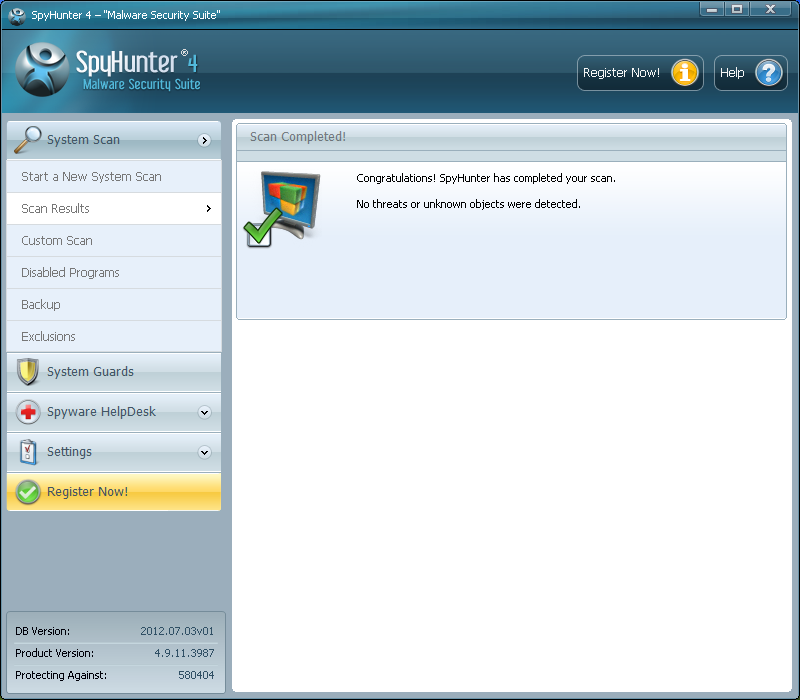
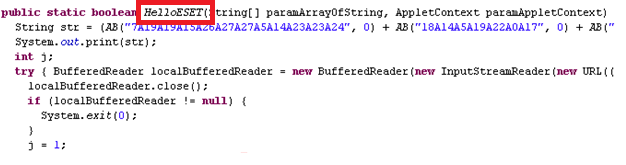
The second tool downloaded – “SpyHunter-Installer.exe” – installs SpyHunter4 from a company named Enigma Software Group (ESG), located in Clearwater, Florida. This anti-malware program had just one small problem in this context: in our tests, it did not detect ACAD/Medre.A on an infected system.
Now there is no anti-malware solution that will always detect all threats all the time, though we try our best at ESET to accomplish that. However, if the program is advertised specifically as suitable for the removal of ACAD/Medre.A then in this case, that claim is dubious at best. Note that the dubious claim here is made by Clean Guide PC, and not Enigma Software Group.
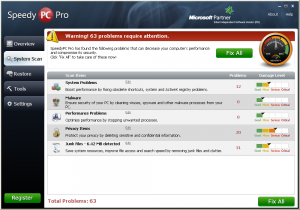
The third program downloaded is “SpeedyPC Pro Installer.exe”, and this utility found a mere sixty-three (63) problems that required my attention. Not bad for a clean – fully patched – disk image of a PC running Microsoft Windows with a sole ACAD/Medre.A infection. What is bad is that this program, also advertised as part of the Medre.A removal process, does not detect the malware either, as shown in the picture below.
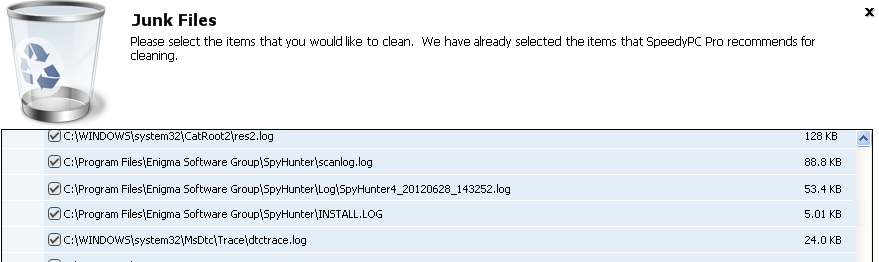
Funnily enough, the Junk Files section lists the install and processing logs of SpyHunter4. You would expect that – if offered together as a solution – these programs would interact with each other cooperatively, rather than the one calling the other “Junk”.
Of course, if you want to fix any of the problems with either SpyHunter4 or SpeedyPC Pro, then you first need to register (and thus pay) for the programs. As neither of the two tools will actually clean ACAD/Medre.A from my system, I will not be doing that. But since I want to have a clean system, and since the CleanPC Guide also takes every opportunity to suggest that I chat to a Live Expert 24/7, why not try that?
Oops… Clicking on any of the images that tell me to click to chat informs me that they currently are not available for a chat! So far it seems that “Live Help 24/7” is not actually open for business at the weekend.
But when they were finally open for business I “tried” them and found myself chatting to “James” who wanted me to pay $119 to remove all kinds of malware for an entire year. This might be money-well-spend if one had to deal with some really nasty infections (if it was truly effective ![]() , but then again, your ESET product will also do this for real without any additional charge. Tellingly, they did not really know the page I was looking at. If you see the video you will notice the long pause after I ask if the website is theirs… They obviously had to look at it first! And of course it distracted them by forcing them away from their script.
, but then again, your ESET product will also do this for real without any additional charge. Tellingly, they did not really know the page I was looking at. If you see the video you will notice the long pause after I ask if the website is theirs… They obviously had to look at it first! And of course it distracted them by forcing them away from their script.
And, of course it really got interesting when I asked them how they got their technical analysis data as “James” replied that they do not have ANY details “as they are just supporting customers via chat”. Now how can anyone support me without having technical analysis data readily available?
He kept wanting to know if I wanted to purchase their service. Eventually I told him I didn’t, then introduced myself and told them all the information was bogus! I was graciously thanked for the information and told he would forward the information to his superior. I informed him that removing ACAD/Medre.A is not really rocket-science and all what is needed is to remove the infected “*.fas” files (there is somewhat more to clean up, in the registry but not that much) and I got another universal “Okay!”
I don’t know if the chat service is genuine or not but it seems they are clueless.






 Just for kicks I searched my email archive and came up with this gem, the welcome message I received after signed up with Associated Content. This message suggests that Associated Content did not have the right approach to security back then (the original email displays the password in plain text).
Just for kicks I searched my email archive and came up with this gem, the welcome message I received after signed up with Associated Content. This message suggests that Associated Content did not have the right approach to security back then (the original email displays the password in plain text).
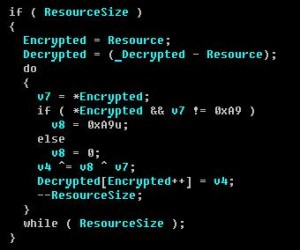
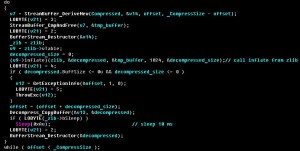
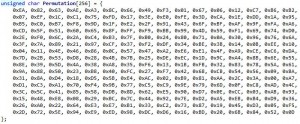


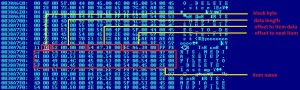

















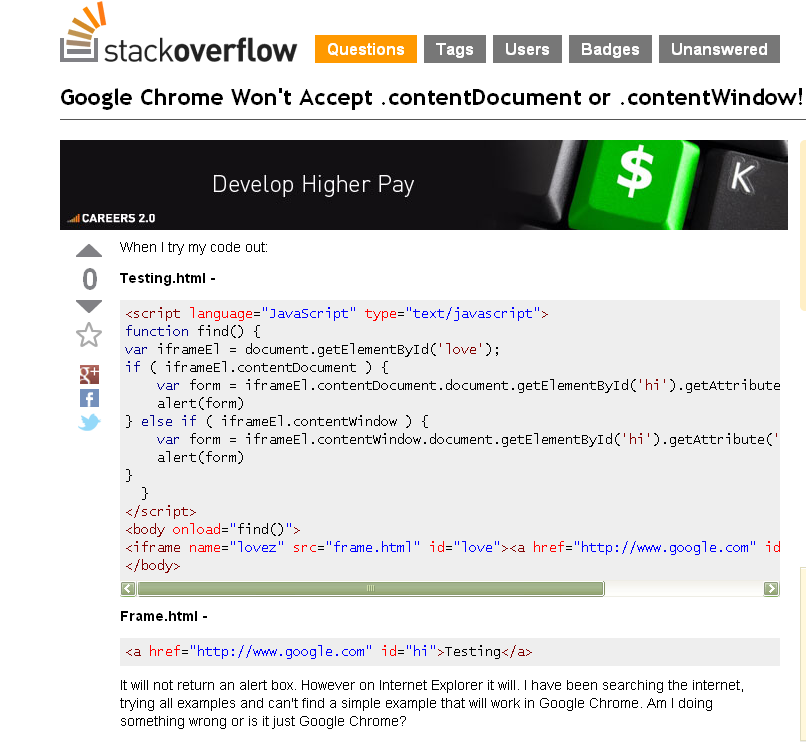
 It turns out that Apache, the most common web server in the world, has an arrangement where it hands off PHP-based requests within .htaccess to PHP itself, which has been working fine on millions and millions of websites for years. But with .htaccess, you can specify WHAT requests get sent to PHP to try to interpret. The usual methods are GET and POST, but if you feed the .htaccess process some non-standard input, PHP automatically (unless otherwise instructed) treats it as a GET request, and allows the utility to start saving the PHP files on a webserver to your local filesystem.
It turns out that Apache, the most common web server in the world, has an arrangement where it hands off PHP-based requests within .htaccess to PHP itself, which has been working fine on millions and millions of websites for years. But with .htaccess, you can specify WHAT requests get sent to PHP to try to interpret. The usual methods are GET and POST, but if you feed the .htaccess process some non-standard input, PHP automatically (unless otherwise instructed) treats it as a GET request, and allows the utility to start saving the PHP files on a webserver to your local filesystem.
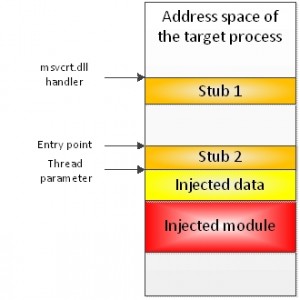
 There has been persistent conjecture regarding the possibility of ‘hardware backdooring’ for as long as I’ve been on the fringes of this industry, and certainly before I had any kind of reputation to risk by joining in.
There has been persistent conjecture regarding the possibility of ‘hardware backdooring’ for as long as I’ve been on the fringes of this industry, and certainly before I had any kind of reputation to risk by joining in.











 From proof-of-concept hacks on the boot loader sequence (EFI), where rogue drivers could potentially be hooked into and used to wreak havoc on OSX, to firmware flashing and other low level hacks, running the gamut to app security, and kernel heap as well, the spotlight squarely focused on Mac OSX and iOS. A few years ago Mac sessions were far more rare, so does this mean the age of Mac hacking has arrived?
From proof-of-concept hacks on the boot loader sequence (EFI), where rogue drivers could potentially be hooked into and used to wreak havoc on OSX, to firmware flashing and other low level hacks, running the gamut to app security, and kernel heap as well, the spotlight squarely focused on Mac OSX and iOS. A few years ago Mac sessions were far more rare, so does this mean the age of Mac hacking has arrived?

 As news spread last weekend about how much of Mat’s data the hackers had wiped out–by social engineering Apple Support into wiping his iPhone, iPad and MacBook–the company quickly moved to suspend over-the-phone resetting of Apple ID passwords. Amazon also reacted and,
As news spread last weekend about how much of Mat’s data the hackers had wiped out–by social engineering Apple Support into wiping his iPhone, iPad and MacBook–the company quickly moved to suspend over-the-phone resetting of Apple ID passwords. Amazon also reacted and, 







